The proliferation of smartphones has been a boon to business as well as a potential logistical nightmare. Not only do these devices require their own IT policies and management, but by the nature of simply existing, they present an additional security risk to businesses that may not be prepared for the vulnerabilities they can introduce.
While mobile device security has come a long way in recent years, there are still potential flaws in security that malicious individuals can exploit to gain access or control to secure data. Many of these openings will often come down to how security savvy the end-user of the device is; there’s not much a manufacturer can do if their customers willingly visit unsafe sites or click links that may contain malware. Some of these cases can be mitigated at the software level by built-in securities in the device’s operating system, but there’s still no excuse for proper security training at the enterprise level.
In addition, manufacturers are in a constant arms-race against hackers to protect their devices at the hardware and software levels to ensure a secure mobile experience. The security of the device’s operating system, the frequency of security patches, and the built-in hardware prevention measures are key to the overall security of a mobile device. Devices that are configured to be ready for MDM integration give business’ an additional advantage over devices without it.
Today we’re looking at a list of secure consumer smartphones that can be found in the workplace, the level of security they offer, and the reasons why they’re smart choices for consumers. This list excludes several phones that may offer a higher level of security, but are either hard to find, prohibitively expensive, or designed from the ground up as executive-level security devices. As such, certain phones – like the Blackphone – will be excluded from this list.
Blackberry KEYone
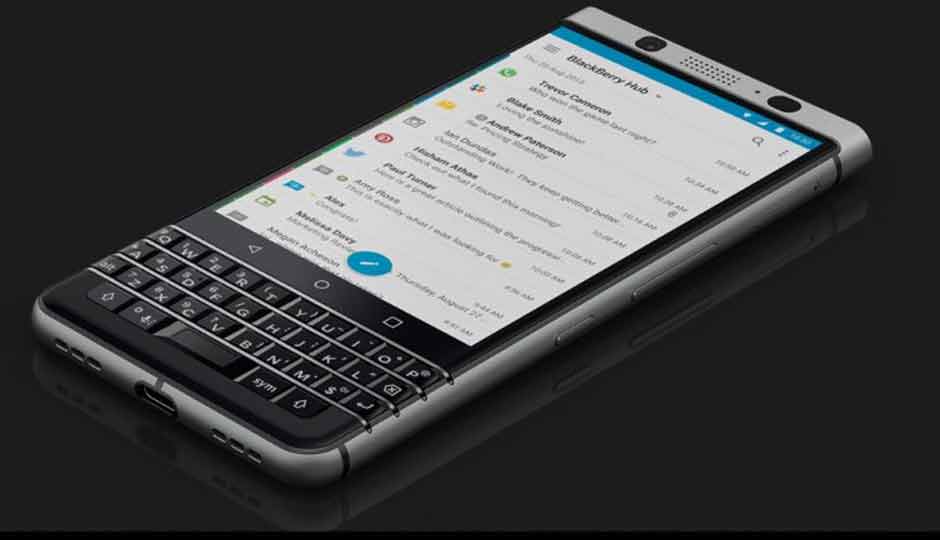
The only device on this list that uses full hard-disk encryption, Blackberry phones have been an established name in secure devices for years. Comparatively inexpensive to the other phones on this list, the KEYone gains a number of security advantages gleaned during the transition from the old proprietary Blackberry OS to the base Android operating system.
While fans of phone modification will be disappointed that the KEYone’s security features have effectively removed the ability for the phone to be given root access, this process of hardware-based cryptographic keying and scanning makes the KEY one an incredibly secure device. Every time the device is turned on, cryptographic keys are generated an injected directly into the CPU. These keys are checked through several layers of the device’s system, verifying no alterations have occurred and protecting against device tampering. The keys are then scrambled in the device’s memory, resulting in the aforementioned inability to root the device.
Blackberry is also zealous about security patches, patching security openings as soon as they are found, in addition to the monthly Android security patches provided by Google.
If there’s one downside to the KEYone, it occurred in the transition to the Android operating system. The Linux-based Android OS is one of the most widely used operating systems on the market today, and hackers will target their software at the Linux kernel for this reason. Regardless, when it comes to Android-based consumer devices, the KEYone comes out on top.
Pixel 2/2 XL
![]()
Google’s flagship Android smartphone, the Pixel 2 gets preferential treatment when it comes to patches, operating system updates, and security development. This fact alone gives it a small edge over other Android phones, but Google has gone one step further, borrowing from Blackberry’s award-winning security practices in its own unique way.
Similar to the way other flagship phones deal with security, the Pixel 2 combines software and hardware solutions to its security procedures. Unique to the device, however, is the removal of the software-based “Trust-Zone” utilized by most other Android phones. Instead, the Pixel 2 moves its key verification process to a separate chip that’s physically removed from the device’s SoC.This provides an additional level of security for the systems validation cryptography keys above and beyond what other phones that combine these processes offer.
Google also offers a lucrative Bug Bounty program to developers, providing additional incentive for enterprising individuals to find flaws in their software and hardware.
iPhone X

Gaining a majority of its security advantages thanks to its proprietary OS – and the fact that only iPhones run it – the iPhone X is one of the most secure consumer smartphones available today. The speed with which Apple can deploy patches, operating system updates, and security fixes is vastly superior to Google’s Android operating system, due to the sheer number of different devices, skins, and versions the Android OS comes with.
Apple also takes a controlled approach to file encryption, giving them more precise manipulation of device security. Multiple-layer file encryption, with the ability to set four different classes of security keys, means iPhone users get the benefits of both security and accessibility on their devices. Common Vulnerabilities and Exposures (CVEs) found on iOS are also far fewer than those found on Android, and quickly patched to prevent a security risk.
The recent storm caused by the FBI’s desire to crack the encryption found on an iPhone lends additional credence to the idea of Apple device security being top-notch. It’s one of the most secure widely available non-Android smartphones available today.
Security Begins and Ends With You
In the end, the most secure device in the world can still be open to intrusion if the end-user is careless. While the above-listed options certainly rank high in the world of secure devices, the steps the developers have taken to protect your data won’t go very far if you aren’t up to snuff on your security basics. Always keep updated on the latest security practices – for both company and private use – to ensure your data stays out of the wrong hands.
